I ran some very basic simulations to access if the DAO can be ‘taken hostage’ by a select number of delegates by triggering on-chain votes with sufficient quorum of 1,000,000 votes. @AvsA pointed out that the top 5 delegates make up for sufficient quorum. I generalised the process to N number of delegates (‘colluders’) over the list of top 50 delegates scrapped from Sybil.org. The top 20 delegates are listed below for quick look-up:
1 brantly.eth 5.362 367162
2 coinbase.eth 4.840 331375
3 nick.eth 4.149 284107
4 she256.eth 4.065 278319
5 cory_eth 4.000 273907
6 avsa.eth 3.245 222209
7 lefteris.eth 3.202 219252
8 rainbowwallet.eth 2.986 204457
9 fireeyesdao.eth 2.493 170668
10 mikedemarais.eth 2.418 165575
11 griff.eth 2.417 165522
12 simona.eth 2.342 160346
13 ChainLinkGod 2.197 150455
14 superphiz.eth 1.996 136646
15 imtoken.eth 1.719 117721
16 keikreutler.eth 1.349 92342
17 maaria.eth 0.975 66762
18 devdao.eth 0.913 62496
19 marspunks.eth 0.887 60748
20 metaphor.xyz 0.882 60418
The full set of results can be found here. To summarise:
colluders threats
3 0
4 302
5 17920
6 478783
‘colluders’ == number of rogue delegates
‘threats’ == number of possible combinations of rogue delegates with > 1,000,000 votes in total
These results suggest that a vote can be triggered by as few as 4 not-necessarily-top delegates. In comparison, in a utopic world where all 50 delegates have equal votes, quorum cannot be reached unless a minimum of 9 delegates collude.
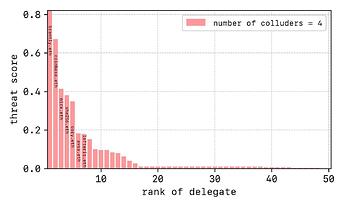
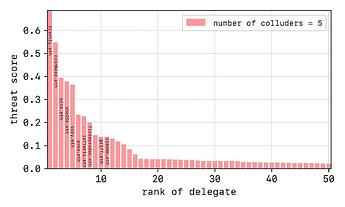
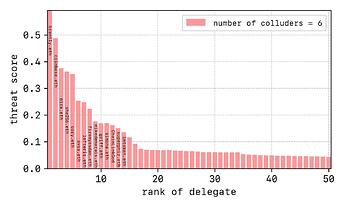
In further detail, in each case I looked for reoccurrence of delegates across all combinations of attacks and gave them a threat score (see below)
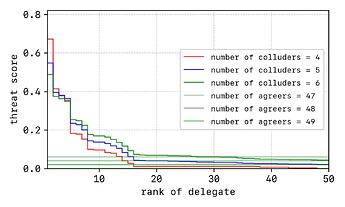
All three cases put together show the expected trend (see below). Notably, when N > 25, ‘colluders’ effectively become ‘agreers’ since now the majority decides the fate of the protocol.