Recent ENS relevant token holder changes
Summary:
There have been a few new wallets with big undelegated balances of ENS, which could be a factor of risk in case of malicious positioning. We’ve found that this looks like a cold wallet reshuffle, and that coinbase would be unable to confirm anything for customer privacy reasons. We don’t evaluate any imminent risk, specially given the security council in place, but will keep tracking the movements of those and any other big holder/delegate changes.
1) Context
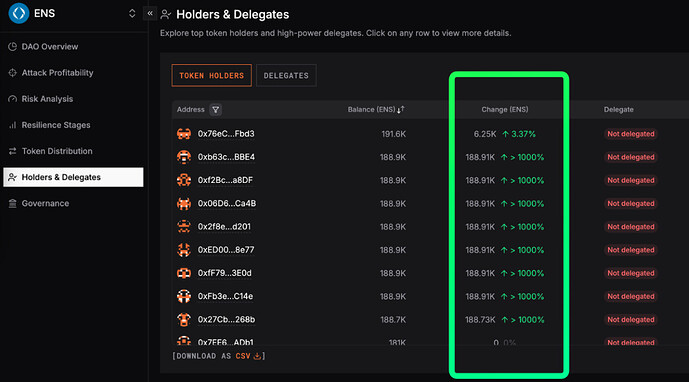
We identified a total of ~2.4M ENS across 13 addresses holding more than 100,000 ENS whose balances increased from 0 over the prior 30 days. Within this set, 11 addresses appear “connected” under a single heuristic: they received ENS sourced from Coinbase in the same block (or via tightly clustered Coinbase batch transactions).
On-chain, 5 transactions are central to the observed inflows. Each transaction is labeled on Etherscan as a Coinbase flow (initiated by “Coinbase: Deposit” interacting with “Coinbase 10”), and each transaction distributes ENS to multiple recipient addresses in a single execution.
Key question: does this pattern reflect (a) normal exchange batching across many unrelated clients, (b) Coinbase internal wallet management, or (c) a single actor (or coordinated actors) capable of directing many high-value withdrawals to many addresses at once?
2) Why does this matter for ENS governance security
ENS token concentration can be a governance risk when a single beneficial owner accumulates a large position and then fragments custody across many addresses to reduce visibility, complicate monitoring, or distribute signing risk. The pattern here (large balances, recent inflows, and clustered Coinbase provenance) is consistent with multiple benign explanations, but it is also consistent with obfuscation by distribution.
This report, therefore, treats the cluster as a monitoring priority, not as a confirmed threat.
Currently, the clusters across the 11 identified addresses total 2.244M ENS. This represents 56% of ENS DAO’s delegated supply and ~1.4x its active supply.
In other words, the voting power held by the addresses that experienced a sudden increase in ENS balances over the last 30 days is nearly double the DAO’s active voting power. It would take 56% of all delegated votes to block a malicious proposal if these addresses were to submit it and vote in favor.
With ENS’s average turnout at 1.4M ENS, the DAO could be at risk if these addresses are controlled by one or multiple malicious actors.
3) On-chain Analysis
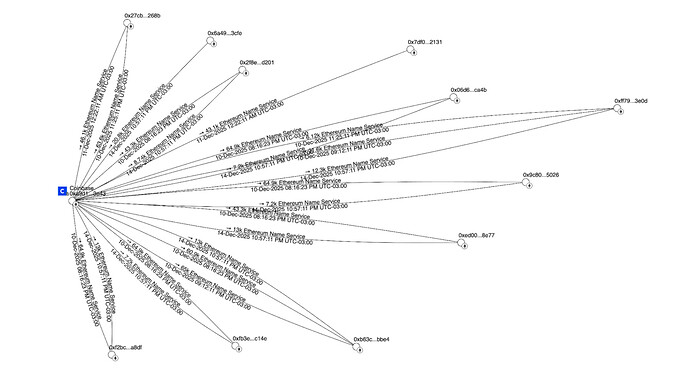
Map of Coinbase-originated transactions that sent $ENS to 11 addresses on different days. Visualization available on Breadcrumbs.
Five transactions were executed from addresses identified as Coinbase wallets:
Transaction 1
Transaction 2
Transaction 3
Transaction 4
Transaction 5
Each transaction contains multiple outbound transfers (i.e., batched distributions), including transfers involving $ENS. In total, 11 addresses received 2.244M $ENS between November and December 2025 across these five transactions. The recipient addresses are:
1 - 0xfF79bBf6EC5729dFc095664a00c5c0f8E4613E0d
2 - 0xFb3ef12f7792600a20a93A633D87448a87C4C14e
3 - 0xf2Bc77093395e2Ff844A218773d4a35b5178a8DF
4 - 0xED0062AB7E2699D89959b0a55efAfEb6202C8e77
5 - 0xb63c0858AA983562F064D7678bd30415669dBBE4
6 - 0x2f8ee284219E6B9d2dC080de75831fC60ff7d201
7 - 0x06D6f3f9db90c77b53481246768B9Faf986FCa4B
8 - 0x27Cb73Fed870CDdfd782dF16518466316782268b
9 - 0x7Df0Ff2E8D2d8bF6e4AE42bcAF05b62f85142131
10 - 0x6A496c6076A1F3ca554b6F4eEf81e4885A433cFE
11- 0x9C80d042dB8cDd2586F00FA8ed47c387dFd05026
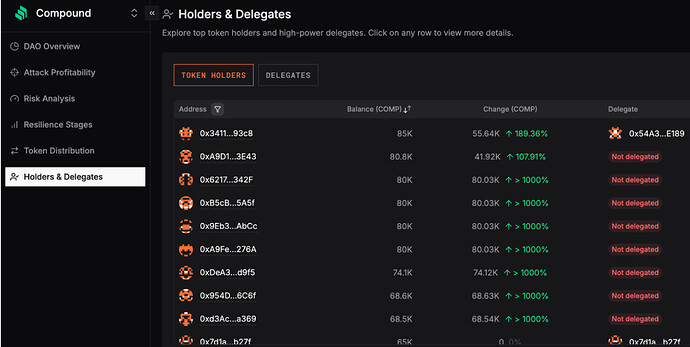
Beyond $ENS, some of these batches also include other governance tokens, such as $COMP. Notably, $COMP exhibited a similar pattern: certain addresses saw a sudden year-end balance increase driven by batched transfers originating from addresses identified as Coinbase wallets.
4) A Similar Pattern Observed in Compound
Currently, Compound governance has a known individual/entity associated with DAO attacks: Humpy.
Last year, we mapped 27 addresses connected to Humpy, which he has used to attempt to block or pass proposals within Compound governance. It is reasonable to say that, today, Compound has been partially captured by Humpy.
At first glance, Humpy would be the most obvious candidate to attribute control of these $ENS-holding addresses. However, there are several differences in Humpy’s modus operandi, including: (1) the use of exchanges such as KuCoin, MEXC, and Bybit, which are headquartered outside the United States, and (2) Humpy’s transfers are typically not batched. They are usually executed as individual withdrawals, separated by measurable time gaps.
As a result, while the behavior resembles Humpy’s broader pattern when attempting to capture other DAOs, there are practical differences between his historical activity and what we observed across the 11 addresses linked via Coinbase-originated transactions.
5) What about the other two addresses?
As discussed initially, 13 addresses increased their $ENS holdings over the last 30 days, 11 of which were covered in the cluster described above.
The remaining 2 addresses are:
-
0x8Fa4EE1776032B612206E754eC2382b534D4ac6F (connections to Galaxy Digital and Galaxy Digital OTC)
-
0x525869AD2488101b5cf47e0D898a59f029b32b03 (connections to addresses related to Jez San)
Because we were able to identify them, and because they do not share provenance or linkages with the 11-address Coinbase distribution set and are not newly created wallets, we did not include them in the previously analyzed cluster.
6) Investigation and Next Steps
We got in touch with Coinbase employees to understand whether this batch pattern reflects the exchange’s internal wallet/key management practices. They couldn’t provide any direct information on the case for privacy reasons, but pointed out that a cold wallet reshuffle could have a similar pattern.
We will keep track of those addresses movements, while we assume they don’t represent direct risk at the moment (given the security council and the likelihood of being normal CEX operations), they are still capable of being hard to defeat if used maliciously.