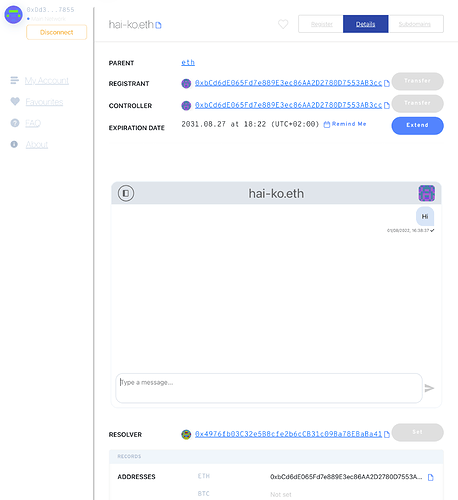
Hello! We are the team of dm3 protocol that presented on the Ecosystem WG call, and we would love to have the feedback from the ENS community and research any possibility of integration! Down below is an explanation of our protocol! Thanks!
Current stage
With the rise of web3, self-sovereign identity management and non-custodial key management have gained a lot of attention again. There are millions of people controlling their own keys through wallets such as MetaMask and others. The introduction of the Ethereum Name Service (ENS) has given us simple names, such as alice.eth, which we truly own. But not only that: It is a public record secured by private keys which can contain more than a simple domain name. It can also host public keys used for encrypted communication. Only the actual owner of the ENS domain can change the registered public encryption and signing keys, and there is an immutable record secured by global consensus around all changes and its most current status. This is the basis for secure encrypted communication in web3, tied to the web3 username: Your ENS domain.
What is dm3?
dm3 allows you to easily write a signed and encrypted message to another ENS domain owner, such as alice.eth, without having any single point of failure.
We will walk you through the steps and components of DM3:
Initial Sign-In
Alice owns her name: alice.eth. Nobody can take it from her as long as she keeps the associated ethereum account key secure.
When dm3 is first used, public signing and encryption keys are generated based on the key in her Ethereum wallet (MetaMask, WalletConnect, …). The associated private keys can be regenerated at any time using the key in the Ethereum wallet.
In addition to those public keys, Alice provides an URL to the delivery service. The delivery service is responsible for forwarding and notifying the recipient when messages arrive. This service can run on her server or be provided by a third party. This service cannot read or modify the messages since they are signed and encrypted. The public keys and the delivery service URL are made public using an ENS text record.
Message Storage
The location where the messages are stored can also be freely chosen. It can be locally in the browser (not recommended, since the browser storage can get deleted from time to time), a local file, IPFS (web3 storage), or the user’s own personal cloud. Even if the user opts for a centralized cloud provider such as GDrive, Google has no power to read or manipulate messages or gain any control over the user’s account/ENS Domain.
Summary
In summary, the core of dm3 are the published text records on ENS that provide the public encryption and signing keys. On top of this, the user can choose self-hosted or third-party hosted service providers that act as delivery services and/or storage providers.
app.dm3.network also offers those services, but the user is in no way bound to use any of them.
Guiding principles
The principles in the design of dm3 are:
- Decentralization as in
- works without us, and the user is free to choose and change a service provider or host all the services themselves
- Non-custodial - your keys, your messages
- Key revocation/rotation securely done as ENS text records, verified by global consensus on Ethereum
- “can’t be evil” - we cannot read, delete, censor anything you do within dm3
- fully open source (BSD 2 license)
ENS Integration
dm3 is designed after the same principles as ENS. Therefore it could be more tightly integrated with the ENS app. As a first step, the ENS app could show the eth.dm3.profile text record value. In a later stage, the ENS app could directly integrate the dm3 widget into the details page of an ENS name.
dm3 Protocol
 Delivery Flow & API
Delivery Flow & API
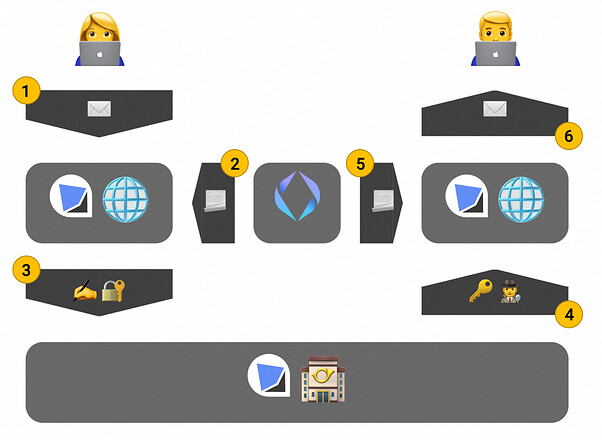
The following example depicts how the delivery would work if Alice sent a message to Bob.
- Alice types her message for Bob into the dm3 App and submits it.
- The dm3 App asks on-chain for Bob’sdm3 profile. To do so,the app queries the eth.ens-mail text record linked to his ENS name. The profile contains Bob’s public encryption key, his public signing key, and the URL to the Delivery Service heuses.
- The message content is signed using Alice’s private signing key and encrypted using Bob’s public encryption key. After the message is encrypted, it is sent to the delivery service used by Bob via its WebSocket API.
- The delivery service pushes the message to Bob’s instance of the dm3 app. The app decrypts the message using Bob’s private encryption key.
- The app queries Alice’s dm3 profil and uses it to check whether the message signature is valid.
- If the signature is valid, Bob is able to read the message
There is no central delivery service. Alice and Bob can change their delivery service by changing the delivery service URL in their profile. They could, for example, run a delivery service instance on their DAppNode at home.
 Key Management
Key Management
The aim of the key management is to give the owner of the key, who controls the corresponding ESN name, complete control over the dm3 identity. No one who does not have access to this key is able to read messages, send messages, or change profile settings.
The following types of keys exist:
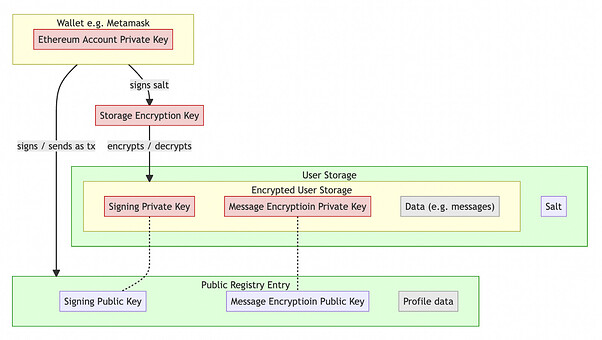
- Ethereum Account Key: The private key of the Ethereum account that owns your ENS name.
- Storage Encryption Key: The symmetric key used to encrypt the user storage. This key is generated by signing a message including a salt with the Ethereum Account Key.
Storage_Encryption_Key = keccak256( personal_sign( salt ) ) - Message Encryption Key Pair: The key pair used to encrypt/decrypt messages.
- Signing Key Pair: The key pair used to sign/verify messages.
 Sign-In Flow
Sign-In Flow
The dm3 app requires users to sign in using their Ethereum account. The initial sign-in consists of the following steps:
- Connect an Ethereum account: The dm3 app connects to an Ethereum Account which is injected by a wallet (e.g., MetaMask).
- Storage Encryption Key creation: A message containing a salt (randomly generated characters) is created and signed with the user’s Ethereum Account Key. The hash of the signature serves as Storage Encryption Key. The salt is stored unencrypted in the user storage.
- dm3 Profile creation: The app generates a new Message Encryption Key Pair and Signing Key Pair and stores the private keys in the encrypted part of the User Storage. The public keys and the delivery service URL constitute the dm3 Profile.
After the initial sign-in, the user can interact with all users connected to the same delivery service. To connect with users of other delivery services, the user must publish the URL pointing to theirdm3 Profile as ENS text record.
Any subsequent sign-in consists of two steps:
- Connect an Ethereum account
- Decryption of the User Storage: The app retrieves the user storage from the selected storage location. The user storage contains the unencrypted salt message and signs it using the Ethereum account to recreate the Storage Encryption Key. This key’s purpose is to decrypt the encrypted part of the user storage.
 Profile Registry
Profile Registry
For the protocol to work, there needs to be one registry where the dm3 App can look up dm3 profiles of other users. dm3 uses ENS text records for this purpose. The text record named eth.ens-mail contains a URL to the actual profile. It is essential to verify the integrity of the profile entry. For example, if the eth.ens-mail text record contains a simple HTTP-URL, it would be possible to hijack the server and change the profile entry. Therefore, the URL must be an IPFS-URL or an URL containing a hash of the entry.
 Storage Management
Storage Management
During delivery, the messages are encrypted withthe recipient’s Encryption Public Key. However, the delivery service deletes the messages after they are delivered. To access past messages, the dm3 app stores the messages in the encrypted part of the user storage. The user storage is a JSON file.
The separation of delivery and storage of messages allows the users to decide on the storage location of their sent and received messages.
Wherever the storage is located, only the user who owns the corresponding Ethereum account key is able to decrypt it.
Further Use Case
The first use case of the dm3 Protocol is to send signed and end-to-end encrypted messages between two ENS name owners. However, the protocol can also be used to create public message feeds for ENS name owners (“decentralized Twitter”).
Give dm3 a try today. If you have any questions, our team is always available to help. You can reach us at ens-mail.eth or hello@dm3.network.
For the latest news and updates about dm3, be sure to follow us on Twitter.